When the Grid Died: A Cybersecurity Learner’s SDR Log
OK... I know what you’re thinking right now:
“This guy said he’d post every 2–3 weeks. What the hell is he doing here now???”
Well, long story short. I was 2 weeks without internet due to an ISP change and Portugal’s lovely bureaucracy. And when I finally got everything back and started bringing the homelab online…
One day later, the Portugal-Spain blackout happened. And unfortunately, I was one of the 60 million people affected by it.
But, just like Jack the Ripper would say: let’s go by parts.
ISP Change & Offline Grind
I was a bit inactive because of a change in ISPs, caused by a personal situation. I had to cancel the old provider and set up a new one under my name. It took about a week and a half to get installed.
During that time, I tried to keep learning as much as I could offline (or barely offline). But 4G was barely enough to load a browser tab. Forget SOC labs, Cyber Range exercises, or remote desktop connections.
(Trust me, trying to load Azure or Sentinel on mobile data feels like playing Doom on a toaster. It makes you question your will to keep trying.)
While I was cut off, I read a lot of SIGINT, SDR, and tactical books, took notes, and brainstormed drafts.
SDR was my savior from total technical boredom. I have the course books from the Radio Society of Great Britain, and my god. They have no right being this good and this technical at the same time.
I’d say my studies in SDR, NFC, RFID, and electromagnetic waves are what saved this offline time from being a total waste.
Back Online. Then Everything Breaks Again
After those 2 weeks, I was finally back online with a new connection (a powerhouse, by the way). The lab was coming back to life. I was catching up on Cyber Range labs, TryHackMe, and getting back into my regular training rhythm.
And then, the bad hit hard.
Portugal’s Blackout

At around 11:33 AM (UTC), I was reading emails and checking the news when the power suddenly cut out.
My mother called to ask if we’d lost electricity. I confirmed. At that point, I had no idea how serious it was. I shut down the lab servers because the UPS wasn’t going to last forever. I didn’t want the equipment to suffer a forced shutdown.
Then I waited.
When I went outside
(YES, I TOUCH GRASS OFTEN)
I saw my mother talking to the neighbors. That’s when I got hit with the news:
The entire country was down.
Radio Wins in Chaos
That’s when my SDR and radios finally got their moment to shine.
I started hearing reports on radio stations that airports and hospitals had stopped operations and were on backup power (not for long). Panic was setting in on the streets. On my VHF/UHF scanner, I picked up communications from banking and emergency services talking about the blackout on open lines.
- Card payments? Gone.
- ATMs? Offline.
- Multibanco National Financial System? Dead.
- Only analog systems and cash were still working.
Even though it wasn’t a zombie apocalypse, I saw some supermarkets completely shut down. Stock ran out in less than 3 hours. Panic had set in.
At that point, all we could do was stay home and listen to the radio to figure out what was going on.
After about 12 hours without electricity, power was restored in my area.
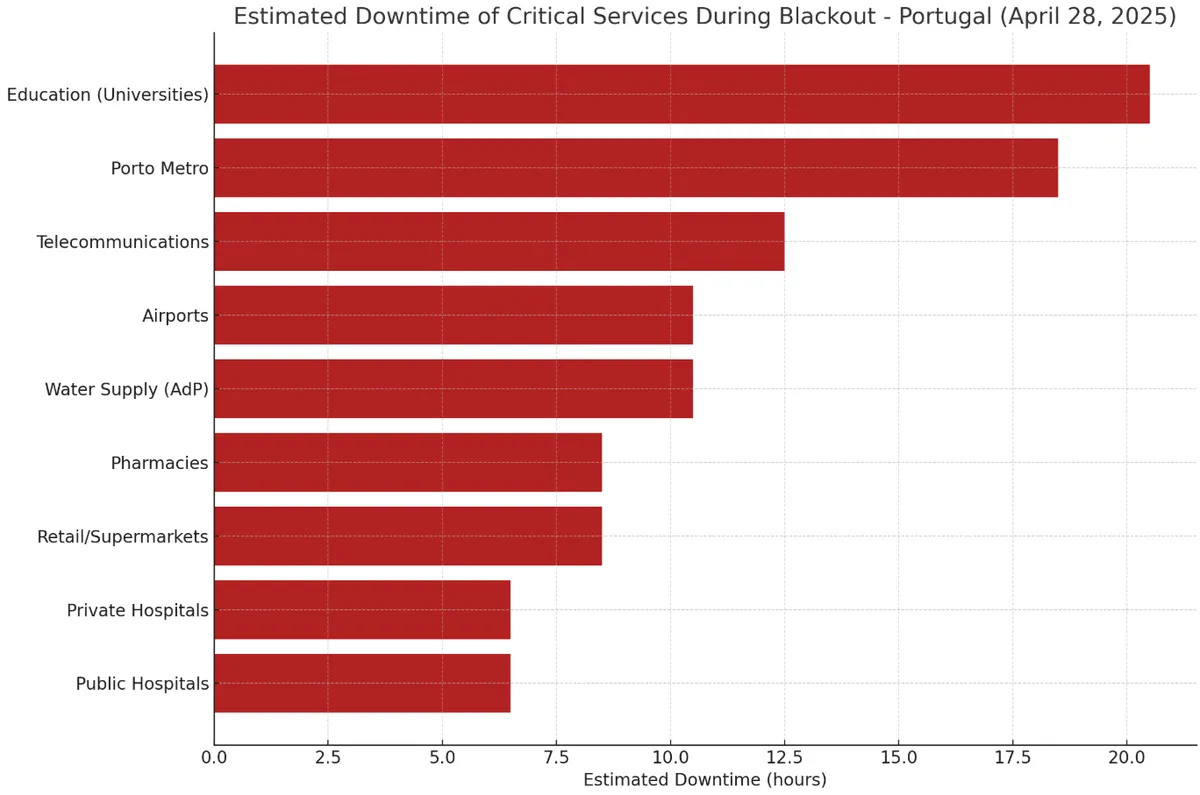
Here’s the estimated downtime in Portugal during the blackout:
Cybersecurity Takeaways
My takeaway as a cybersecurity person?
There was a shocking lack of redundancy and backup operational plans.
Sure, REN (Portugal’s national energy provider) and the Spanish grid operators had incident response plans. If it weren’t for them, power might not have been restored at all.
But private companies, and especially regular civilians, were completely at the mercy of this incident. Even though it was triggered by "natural causes", it was still a serious event.
Some people in local Portuguese cyber communities and among tech enthusiasts are still blaming Russian APTs for the blackout, especially APT28 and APT44.
I don’t have any concrete evidence to support that, but even if it were true, I wouldn’t be surprised. The EU and NATO have already taken serious hits from Sandworm and incidents such as NotPetya.
One Week Later
Almost a week later, I still see banks and shops that don’t have full access to basic services. Some ATMs are completely dead. Some stores are still cash-only due to damaged machines.
This whole thing showed me that my time spent studying SDR and RF wasn’t a waste. It gave me and my family access to information from local and shortwave radio stations. In an incident response scenario, backup communication and information sources are a must.
Final Thoughts
That’s it. That’s what I think of the situation.
I know this isn’t a log, a lab, or an experiment. But sometimes, for cybersecurity or IT professionals, these kinds of real-life incidents are the ultimate test of our incident response and stress management skills.
At the end of the day, there really was a Dino in the Logs.
Thank you for reading.